Everything From The Alerts Plan
With the Protect plan, you get everything from the Alerts plan which includes, an in-depth Cyber Health Check, access to Cyber Watchdog encompassing a full Cyber Security Framework and a Security Awareness Program providing engaging training videos to measure engagement and compliance.

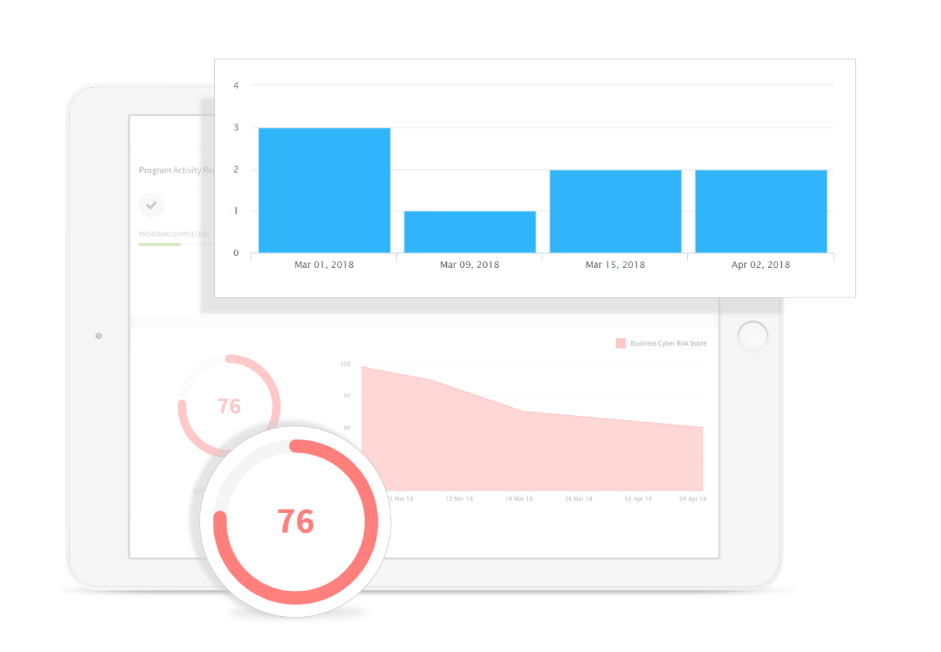
Complete our online cyber risk assessment to determine where your clinic is most at risk. Share these reports internally and benchmark your results with clinics of similar size and/or in similar industries.
Once the risk assessment has been completed, you will have your own risk dashboard where you can track your reduction in risk as you complete toolkit actions.

Start your cyber security journey right! We have collected everything you need to start reducing your cyber security risk. Access our collection of cyber policy documents, operational checklists and market place of preferred vendors.
Each category contains professionally prepared, ready to use policy templates, actionable checklists, and vetted vendors.
 Did you know 90% of breaches are due to human error? It only takes one person in your clinic to click a link or open an attachment for a breach to occur.
Did you know 90% of breaches are due to human error? It only takes one person in your clinic to click a link or open an attachment for a breach to occur.
You can significantly reduce this risk by providing short engaging micro-lessons for staff to learn basic cyber security hygiene.
Perform Regular Spear Phishing Simulations
Our phishing campaigns highlight email phishing risks and train staff on how to avoid them. Send practical simulations to your team to prepare for the email scams targeting your clinic.
Auto-Enroll At Risk Employees
Staff who are phished by the simulation are auto-enrolled into Cyber Watchdog training, which highlights the dangers of phishing and the key steps needed to avoid future attacks.
Real World Templates
Use the same templates that hackers are using. Choose from our extensive library of phishing templates, which is regularly updated to mimic current threats.
Spear Phishing Simulations
Spear phishers pose as trusted contacts to scam their targets. Merge your company information into your phishing simulations to prepare your staff for real attacks.
Advanced Tracking
Our advanced tracking engine provides accurate reporting on all unsafe opens, clicks replies and downloads made within our phishing simulations
Detailed Campaign Reporting
Access reporting that provides insights and action-points based on campaign results. Drill down into specific reports and export data as you see fit for presentations and board meetings.
Quality Over Quantity
Stop sending out generic phishing content. Our campaigns are industry-specific spear phishing content that emulates real-world scenarios and prepares you for realistic attacks.
Phishing Simulations
Phishing simulations allow staff to experience the methods hackers use in a safe and constructive way. Using our monthly phishing campaigns, we’ve seen an average 80% reduction in risk from baseline readings within only 8 months!
Build a Cyber Resilient Culture
With monthly campaign reporting, Cyberwatchdog provides a concise breakdown of each phishing simulation and the staff / departments that are at-risk.
Measure Risk Reduction
Your Phishing Program Runs On Auto-Pilot
Setup your campaigns once and have your phishing simulations run on auto-pilot for 12 months. You’ll receive monthly campaign reports, with at-risk staff being automatically enrolled in phishing awareness training.
Industry Benchmarking & Detailed Reporting
Get detailed reporting from completed campaigns highlighting which staff and departments are at-risk. You can also benchmark your ongoing results with others in your industry.
Our Motto:
Quality over Quantity
On activation, you will be provided with industry and geographically specific phishing templates. Simply select from a hand-picked collection of high-quality email templates and start your campaigns.
We detect even the most concealed activities and utilise machine learning technologies to identify unknown threats, lateral movement and malicious insider behaviour.
Endpoints
Advanced endpoint visibility forensic analysis of endpoint telemetry, taction and response.
Network
Detect insider threat and lateral movement with network based intrusion detection and packet analysis.
Cloud
Mutli-cloud security insights, cloud workload vulnerability management and continuous risk assessment.
_Osint
Continuously integration open source intelligence, including indicators from Dark Web, social media and third-party vulnerabilities.
_Anything
A standard or custom application or log source, completely integrated into the platform.
Automated Threat Intelligence
Cyber Protect brings automated and integrated threat intelligence and expert human security-analyst threat hunting including:
Lateral Movement
Command & Control Traffic
Backdoors and Tunnels
Malware and Botnet Connections
Internal Port Scanning and Reconnaissance
Password Brute Forcing
Insider Threats
Impersonation and Spoofing Attacks
Exploitation Attempts
Unauthorised Remote Access Tools
Rogue Devices
